
The pharmaceutical industry is known for its meticulous regulation, and plays a crucial role in creating life-saving medications that enhance millions of lives across the globe. Companies within the industry are leveraging cutting-edge technology to propel research, development, and patient care, placing themselves at the forefront of a digital revolution. However, With the escalating reliance on technology and the ever-expanding interconnectedness of global supply chains, the industry is facing a rising and concerning threat: cyberattacks.
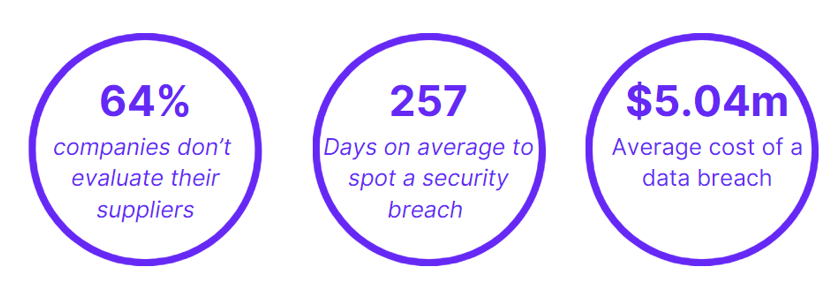
Traditionally, the pharmaceutical industry along with many other industries take a reactive stance towards cyber security. Although some companies are starting to look at their cyber strength, it is common for companies to only react and turn focus towards cyber after being the target of an attack. However within the Pharmaceutical industry it takes an average of 257 days to identify and contain a breach. During this length of time a hacker is likely to have had access to systems and visibility of important data. This paired with the average cost of a pharma data breach being $5.04m means that companies can’t afford to take a reactive approach. To mitigate these risks, Pharma companies must recognise their threat landscape and the high probability of an attack. By doing so, they can proactively address potential vulnerabilities before it’s too late. Below we explore five cyber threats that Pharma businesses should be look
5 significant cybersecurity threats that pharmaceutical companies face:
Third-party vendors:
It now goes without saying that that your security is only as strong as the weakest point in your supply chain. Pharmaceutical companies are no exception to this rule as they often operate complex supply chains. Having these heavily interconnected supply chains that lack end-to-end visibility cause multiple blind spots within a company’s security. Any vendor that lacks robust cybersecurity measures, becomes a potential entry points for cyberattacks. Hackers may compromise the vendor’s systems to gain access to the pharmaceutical company’s network, potentially leading to data breaches or intellectual property theft. There might also be vendors may that holds the companies sensitive data and therefore are a significant security risk.
A recent global survey of 2,200 IT decision-makers found that although 84% of respondents were aware of the looming threat posed by supply chain attacks, surprisingly only 36% took the initiative to evaluate new and existing suppliers in the past year. This gap between awareness and action may be due to a lack of necessary resources or tools. It also emphasises the need to close this gap and tackle the challenges associated with protecting against supply chain attacks.
Mergers and acquisitions:
The pharmaceutical industry frequently experiences mergers and acquisitions, which can introduce cybersecurity vulnerabilities. When two companies combine their operations, integrating their IT systems can be complex and challenging. This process often creates security gaps and inconsistencies, which cybercriminals can exploit. Additionally, former employees of the acquired company may still have access to systems, posing insider threats if their access is not properly revoked.
When two companies merge, it’s important to consider compliance, risks, and data protection. This is because one company may have different procedures or be less up-to-date with regulations compared to the other. The same goes for mergers between culturally different organisations, as they may have different cyber postures and risk management approaches. It’s crucial for both companies to align and be clear with each other before a merger takes place.
Employee error:
Human error accounts for over 80% of cyber incidents and remains a significant cybersecurity threat in pharmaceutical companies. Despite advanced security measures, well-intentioned employees can inadvertently undermine the strongest defences. Human error often takes the form of unknowingly clicking on phishing emails, downloading malicious attachments, or sharing sensitive information with unauthorised individuals.
Training and awareness programs are crucial in mitigating this threat, as they can educate employees about the importance of cybersecurity and keep them up to date with the lates best practices and threats.
IoT devices:
The growing use of Internet of Things (IoT) devices in pharmaceutical manufacturing and research introduces new vulnerabilities. While these connected devices offer significant benefits, such as streamlined manufacturing processes and real-time data monitoring, they also introduce vulnerabilities that can be exploited by cybercriminals. From connected lab equipment to remote monitoring of drug storage conditions, these devices often lack robust security features, making them enticing entry points for cyberattacks. Malicious actors might compromise these devices to gain access to the pharmaceutical company’s network, potentially disrupting operations or stealing critical data.
It is vital for companies to effectively manage their IoT assets, ensuring regular checks and prompt updates as soon as they are available. This proactive approach guarantees the maintenance of optimal device performance and security.
Regulatory compliance:
Pharmaceutical companies are obligated to adhere to stringent regulatory requirements, including the healthcare products Regulatory Agency (MHRA) and the General Data Protection Regulation (GDPR). Failure to comply can result in severe penalties. Cybersecurity threats that lead to data breaches or non-compliance with these regulations can have significant legal and financial consequences for companies involved.
The current practice of conducting compliance check-ups annually or every three years is unsustainable in an ever-evolving cyber landscape. The CEO of Black Mesa Labs, Charles Fracchia has emphasised the need for a more robust approach, stating, “At present, compliance is approached through static checkboxes. While we may not expect nuclear sector-level security, we should strive to incorporate checks and balances at every stage, establishing a heightened level of assurance.” Maintaining compliance and keeping to the latest security standards is crucial for companies to mitigate their risk of becoming victim to an attack.

